Let me tell you something about the remoteIoT platform SSH key that's going to blow your mind. Imagine having the ability to control your IoT devices from anywhere in the world, securely and effortlessly. That's exactly what this platform offers, and the SSH key is the golden ticket to unlocking its full potential. In today's hyper-connected world, security is more important than ever, and this platform ensures your devices are protected while giving you the flexibility to manage them remotely.
Now, before we dive deep into the technical stuff, let's break it down for those who might be scratching their heads right now. An SSH key is like a digital key that opens the door to your IoT devices without needing passwords. It's like having a secret handshake that only you and your devices understand. This eliminates the risk of unauthorized access and makes managing your devices a breeze.
So, why should you care about remoteIoT platform SSH key? Well, if you're into smart homes, industrial automation, or any kind of IoT setup, this is a game-changer. It's not just about convenience; it's about safeguarding your digital assets in a world where cyber threats are lurking around every corner. Stick around, because we're about to take you on a journey through the ins and outs of this technology.
- Nfl Universe Football Top Scripts To Dominate The Field
- Danielle Cohn Nude Leaked Onlyfans Instagram Photos
Table of Contents:
- What is RemoteIoT Platform?
- Why SSH Key Matters?
- How SSH Works?
- Benefits of Using SSH
- Setting Up SSH
- Security Best Practices
- Troubleshooting Common Issues
- Advanced Features
- Real-World Applications
- Future of RemoteIoT
What is RemoteIoT Platform?
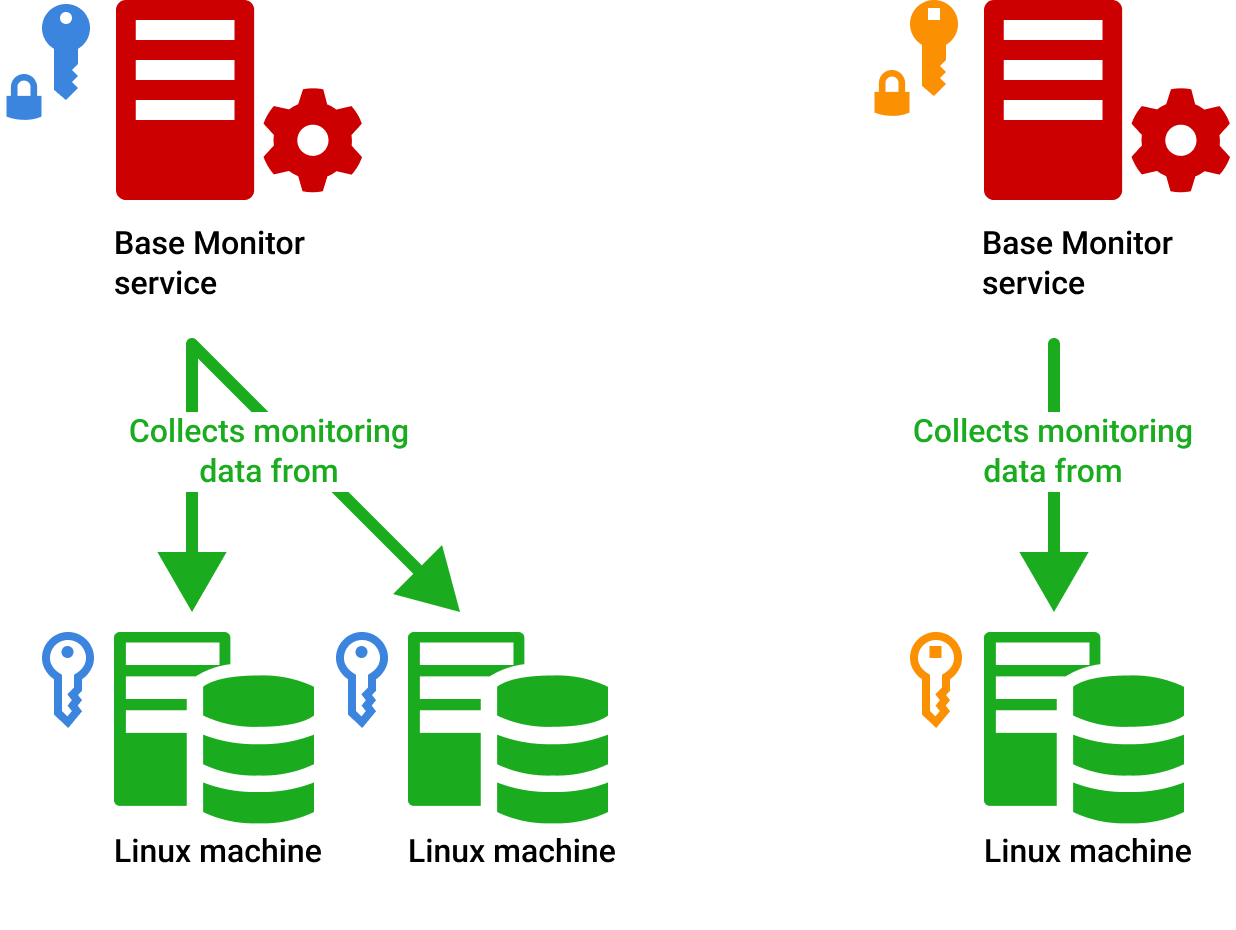
Alright, let’s start with the basics. The remoteIoT platform is like the Swiss Army knife of IoT solutions. It’s a versatile system designed to help you manage, monitor, and control your IoT devices from anywhere in the world. Think of it as your personal assistant that keeps your smart devices in check, ensuring they’re always up and running the way you want them to.
Now, here’s where the SSH key comes into play. This platform leverages SSH to create a secure communication channel between you and your devices. Instead of relying on passwords, which can be easily compromised, the SSH key acts as a digital signature that verifies your identity. This means no one can access your devices unless they have the matching key. Pretty cool, right?
But wait, there’s more. The remoteIoT platform isn’t just about security; it’s also about flexibility. Whether you’re managing a single smart bulb or an entire network of industrial sensors, this platform scales with you. So, whether you’re a tech-savvy individual or a large enterprise, you can trust remoteIoT to handle your IoT needs.
Key Features of RemoteIoT Platform
- Secure device management through SSH
- Scalable architecture for growing IoT setups
- Real-time monitoring and alerts
- Integration with third-party applications
Why SSH Key Matters?
Let’s talk about why the SSH key is such a big deal. In the world of IoT, security is paramount. You can’t just leave your devices out there in the open, hoping for the best. That’s where the SSH key comes in. It’s like having a personal bodyguard for your devices, ensuring only authorized users can access them.
SSH keys eliminate the need for passwords, which are notoriously easy to crack. Instead, they use a pair of cryptographic keys – a public key and a private key – to establish a secure connection. When you try to access your device, the platform checks if your private key matches the public key stored on the device. If they match, you’re in. If not, you’re locked out. Simple, yet effective.
Plus, SSH keys offer more than just security. They also provide convenience. Once you’ve set up your keys, you won’t have to remember complex passwords or worry about resetting them. It’s like having a master key that opens all your doors without the hassle.
How SSH Works?
Now, let’s get a little technical. SSH, or Secure Shell, is a protocol that allows you to securely connect to remote devices over an unsecured network. Here’s how it works in a nutshell:
When you try to access a device using SSH, the platform sends your public key to the device. The device then checks if this key matches the one it has stored. If it does, it generates a random number and encrypts it using your public key. This encrypted number is sent back to you, and your private key decrypts it. If the decrypted number matches the original, the connection is established.
This process might sound complicated, but it’s all done behind the scenes. Once set up, you won’t even notice it happening. It’s like having a secret handshake that happens automatically every time you connect to your device.
Steps in the SSH Process
- Public key is sent to the device
- Device checks for key match
- Random number is encrypted and sent back
- Private key decrypts the number
- Connection is established if the numbers match
Benefits of Using SSH
So, what do you get by using SSH with the remoteIoT platform? Let’s break it down:
First and foremost, you get top-notch security. With SSH, your devices are protected from unauthorized access. Even if someone intercepts your connection, they won’t be able to decipher the encrypted data without your private key. This makes SSH a favorite among security experts and tech enthusiasts alike.
Secondly, you get convenience. No more remembering complex passwords or dealing with password resets. Once you’ve set up your SSH keys, accessing your devices becomes a breeze. It’s like having a VIP pass to your IoT setup.
Lastly, you get peace of mind. Knowing that your devices are secure and accessible from anywhere in the world gives you the freedom to focus on other things. Whether you’re at home, at work, or on vacation, you can rest assured that your IoT devices are in good hands.
Setting Up SSH
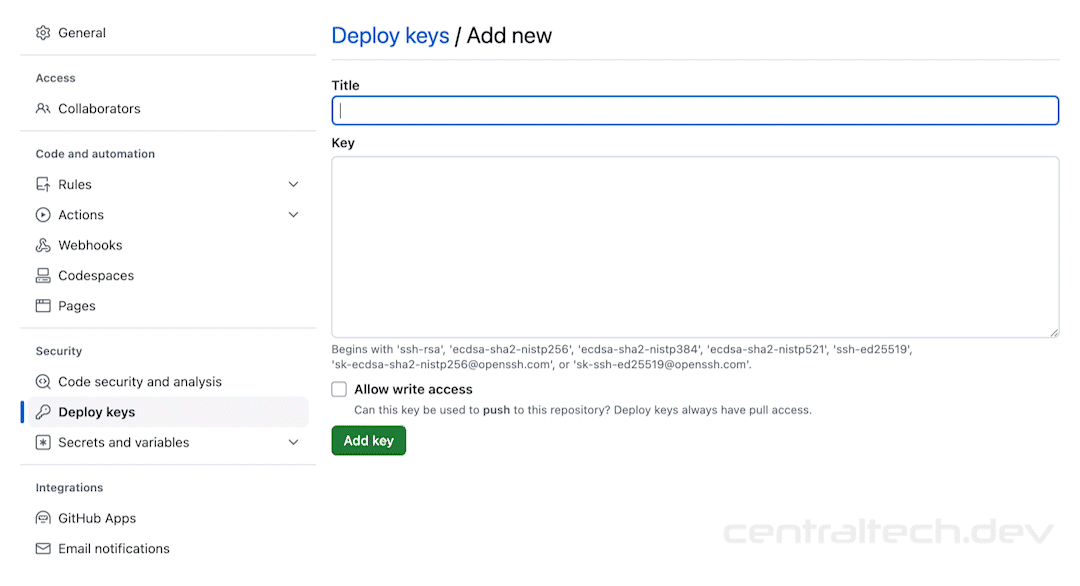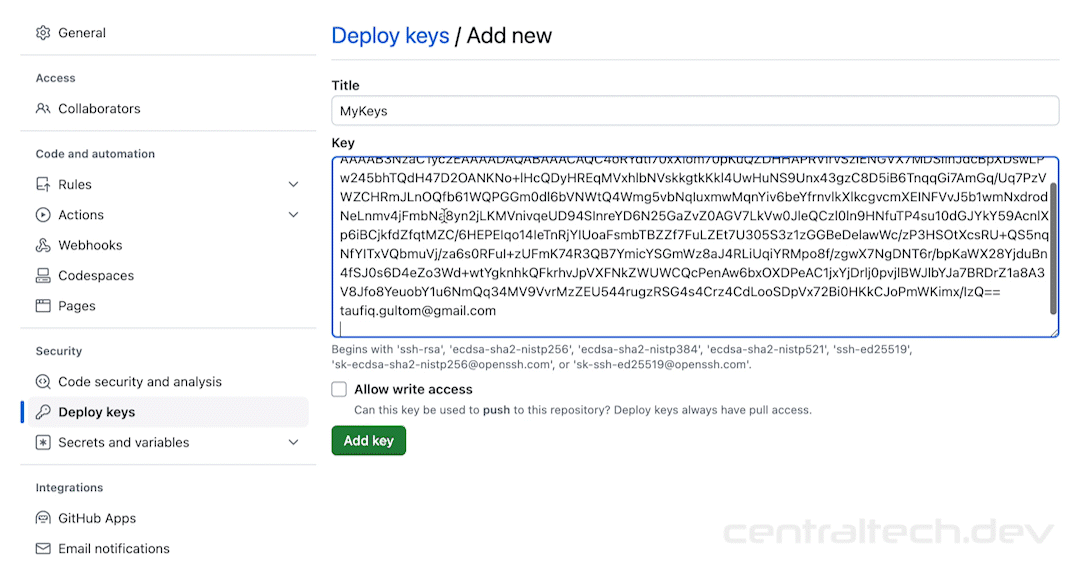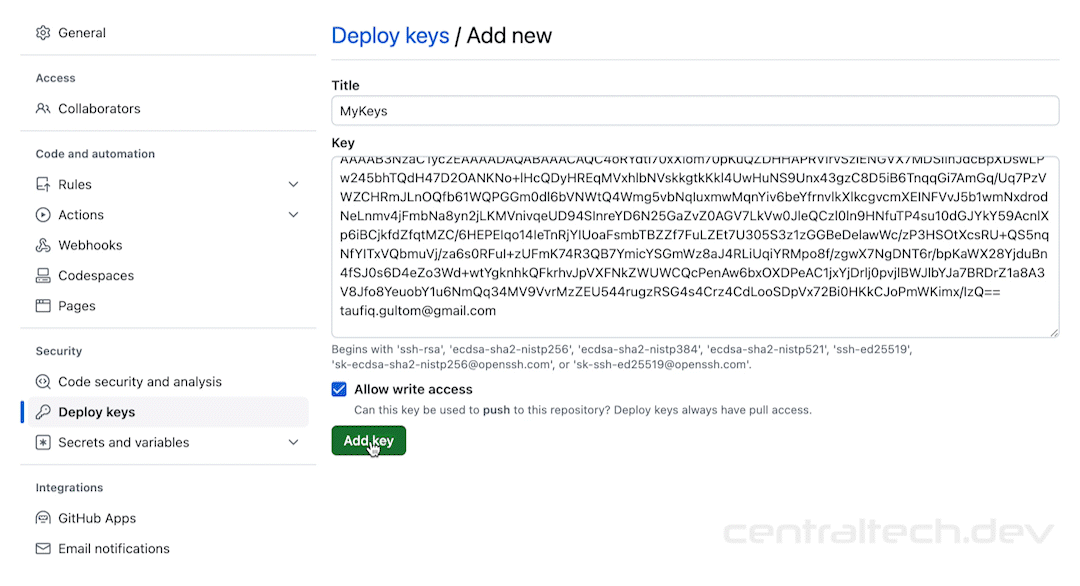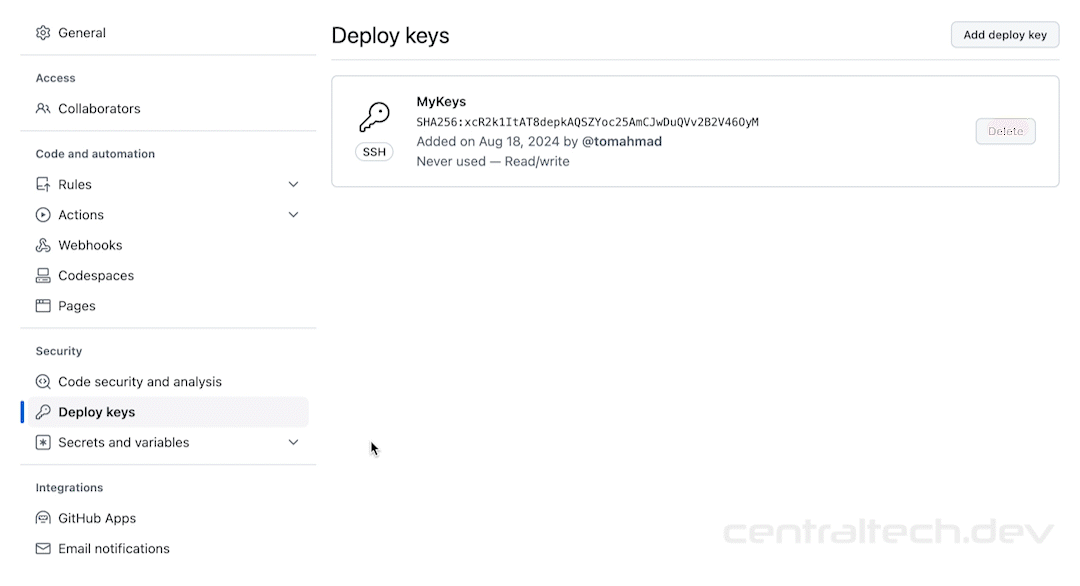
Setting up SSH might sound intimidating, but it’s actually quite straightforward. Here’s a step-by-step guide to help you get started:
First, you’ll need to generate your SSH key pair. This can be done using tools like OpenSSH or PuTTY. Once you’ve generated your keys, you’ll need to add your public key to the remoteIoT platform. This is usually done through the platform’s settings or configuration files.
Next, you’ll need to configure your devices to accept SSH connections. This involves enabling SSH in the device settings and specifying the port number. Most devices use port 22 by default, but you can change this if you want to add an extra layer of security.
Finally, test your connection. Try accessing your device from a remote location to ensure everything is working as expected. If you encounter any issues, don’t worry; we’ll cover troubleshooting in a bit.
Tools for Generating SSH Keys
- OpenSSH
- PuTTY
- SSH Keygen
Security Best Practices
While SSH is a secure protocol, there are still some best practices you should follow to maximize your protection. Here are a few tips:
First, always use strong, unique SSH keys. Avoid using default keys or keys that are too short. The longer your key, the harder it is to crack. Think of it like a lock – the more complex it is, the harder it is to pick.
Second, disable password authentication. This forces users to use SSH keys, which are much harder to crack than passwords. It’s like adding a second lock to your door, making it even more secure.
Lastly, monitor your connections regularly. Keep an eye on who’s accessing your devices and when. If you notice any suspicious activity, investigate it immediately. It’s better to be safe than sorry.
Troubleshooting Common Issues
Even with the best setup, things can go wrong. Here are some common SSH issues and how to fix them:
One common issue is connection timeouts. This usually happens when the device is behind a firewall or NAT. To fix this, make sure the necessary ports are open and properly configured. You might also want to try using a different port number if port 22 is blocked.
Another issue is key mismatches. This happens when the public key on the device doesn’t match the private key on your system. To fix this, re-generate your keys and re-add the public key to the device.
Lastly, there’s the issue of denied access. This usually happens when the device is misconfigured or the SSH service is not running. Check the device settings and ensure the SSH service is enabled and running properly.
Advanced Features
Once you’ve mastered the basics, it’s time to explore some advanced features of the remoteIoT platform. These features take your IoT setup to the next level, giving you even more control and flexibility.
One such feature is SSH tunneling. This allows you to securely access services on your device that aren’t exposed to the internet. For example, you can access a database or web server running on your device without exposing it to the public.
Another feature is SSH agent forwarding. This allows you to use your SSH key on a remote server to access other devices. It’s like having a chain of keys that open multiple doors, all secured by your original SSH key.
Lastly, there’s SSH multiplexing. This allows you to reuse existing connections, reducing the overhead of establishing new ones. It’s like having a fast lane for your SSH connections, making them faster and more efficient.
Real-World Applications
So, how is the remoteIoT platform with SSH key being used in the real world? Let’s take a look at some examples:
In smart homes, the platform is used to manage lighting, thermostats, and security systems. Homeowners can control these devices remotely, ensuring their homes are always secure and comfortable.
In industrial settings, the platform is used to monitor and control machinery. Engineers can access sensors and control systems from anywhere, ensuring smooth operations and minimizing downtime.
In agriculture, the platform is used to monitor soil moisture, weather conditions, and crop health. Farmers can make data-driven decisions to optimize their yields and reduce waste.
Future of RemoteIoT
Looking ahead, the future of remoteIoT platform with SSH key is bright. As IoT continues to grow, so does the need for secure and flexible solutions. The platform is poised to evolve with the times, incorporating new technologies and features to meet the demands of its users.
One exciting development is the integration of AI and machine learning. These technologies can help predict and prevent issues before they occur, making your IoT setup even more reliable.
Another development is the expansion into new industries. From healthcare to transportation, the possibilities are endless. The remoteIoT platform is set to become a cornerstone of the IoT ecosystem, driving innovation and progress across various sectors.
In conclusion, the remoteIoT platform with SSH key offers a secure, flexible, and powerful solution for managing your IoT devices. By following best practices and exploring advanced features, you can take full advantage of what this platform has to offer. So, what are you waiting for? Dive in and start revolutionizing your IoT setup today. Don’t forget to share your thoughts and experiences in the comments below. And if you found this article helpful, be sure to check out our other guides on IoT and cybersecurity.

Detail Author:
- Name : Ola Schowalter IV
- Username : britney.reilly
- Email : jacobs.rebeca@yahoo.com
- Birthdate : 1998-02-12
- Address : 5594 Jonathan Stravenue South Blairside, DC 65979-8691
- Phone : +1-609-858-5214
- Company : Jenkins, Schaefer and Wiza
- Job : Postal Service Clerk
- Bio : Suscipit numquam nam blanditiis minima accusantium error aliquam doloribus. Maxime qui autem dolor. Odio quos excepturi optio velit aut quia. Sequi voluptas possimus et occaecati debitis ullam quis.
Socials
linkedin:
- url : https://linkedin.com/in/valentine.jacobs
- username : valentine.jacobs
- bio : Nesciunt ut provident id consequuntur enim.
- followers : 1407
- following : 1831
tiktok:
- url : https://tiktok.com/@valentine6450
- username : valentine6450
- bio : Inventore assumenda qui aperiam nulla. Ea quis quae et doloribus.
- followers : 450
- following : 771
facebook:
- url : https://facebook.com/valentine8005
- username : valentine8005
- bio : Nemo eos laboriosam voluptatum quam dolore optio aperiam.
- followers : 5056
- following : 1624
instagram:
- url : https://instagram.com/valentine_dev
- username : valentine_dev
- bio : Est tempora quaerat aut beatae libero voluptatem expedita. Odio voluptate nam ipsum ut hic quo non.
- followers : 4130
- following : 2907